Approaches To Message Authentication

Message Authentication Approaches And Using Symmetric Encryption For Message Authentication Message Authentication Code Mac Coursera

Authenticated Encryption Wikipedia
Final Exam Review


Message Authentication An Overview Sciencedirect Topics

Chapter 3 Publickey Cryptography And Message Authentication 1
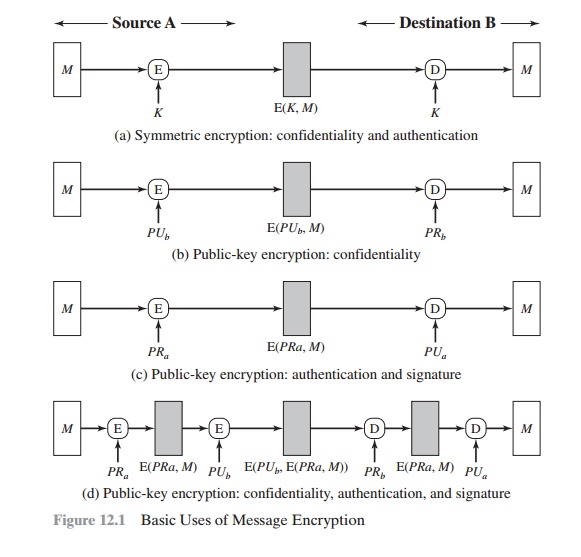
Message Authentication Functions

Chapter 3 Public Key Cryptography And Message Authentication Henric

Unit 2 Public Key Cryptography And Message Authentication Ppt Download

Message Authentication Code Mac Using Java Veracode Blog

Approaches To Message Authentication Youtube
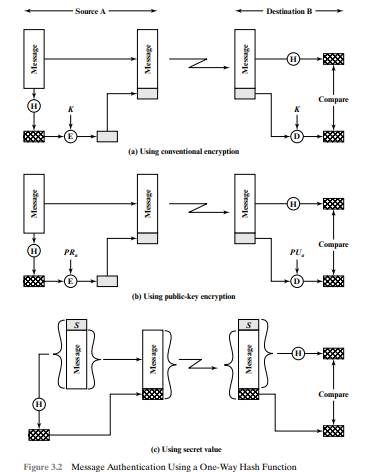
Solved 1 List Three Approaches To Message Authentication 2 What Is A 1 Answer Transtutors
0 Response to "Approaches To Message Authentication"
Post a Comment